Begin the "Define" section by reflecting on what you know and want to know about this "Thing."
As teachers analyze the best digital tools and websites to engage students, they must also address student data privacy involved with using those tools and websites. This "Thing" will help you gain a better understanding of how online resources use student data, so that you can help protect a child's safety ensuring parents and administrators are comfortable with digital learning.
Learning Objectives
Click on each title below to see detailed information.
As you start to investigate the data privacy topic, watch this short video to get an overview. Select image below to view/listen.
There are many aspects of "data" involved in this topic, so before you begin, please take a moment to review these key terms that will be used in this "Thing".
Family Educational Rights and Privacy Act (FERPA) - a federal law enacted in 1974 that guarantees that parents have access to their child’s education record and restricts who can access and use student information.
Children’s Online Privacy Protection Act (COPPA) - controls what information is collected from young children by companies operating websites, games, and mobile applications directed toward children under 13.
Virtual Private Network (VPN) - gives the user online privacy and anonymity by creating a private network from a public internet connection.
Password Manager - assists in generating and retrieving complex passwords with the, potentially of storing such passwords in an encrypted database.
Acceptable Use Policy (AUP) - a document which governs students’ use of the internet at school and covers a wide range of issues surrounding the rights, responsibilities and privileges connected with computer use.
![]()
Now that you have an overview of the data privacy topic and terms, move on to the next section - Digital Footprint.

Image by David Bruyland from Pixabay
A digital footprint can impact your online reputation and image, as well as your reputation in real life. A digital footprint includes anything associated with your name on the Internet and can include personal information. Personal data management is important for your privacy and security and should be modeled for students.
Investigate these resources to learn more.
-
Your Digital Footprint Matters - a free online course from the Internet Society
![]()
Now that you have investigated digital footprint resources, move on to the next section - The Web: Public, Deep, Dark
Different Areas of the "Web"
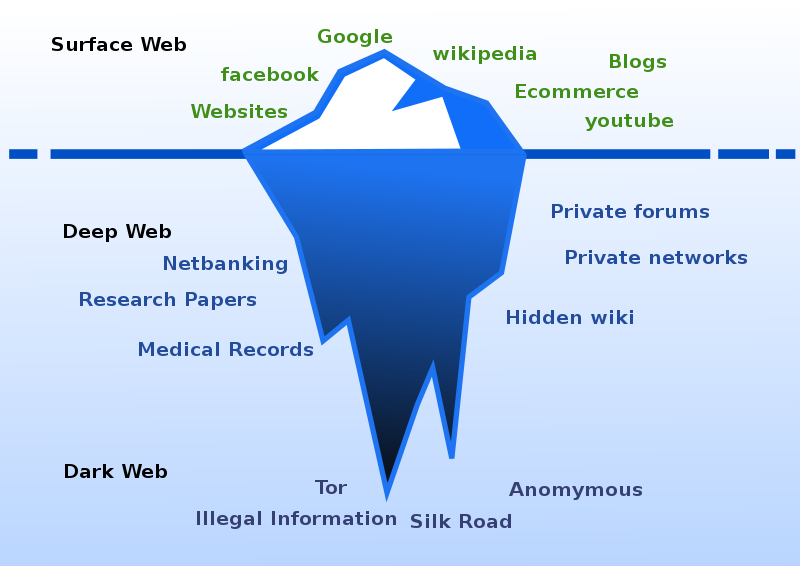
Ranjithsiji / CC BY-SA
Public Web: The information that you would normally find on search engines is available on the public web (surface web). If "Google" can find it, then it’s on the public web. According to Britannica.com, this information makes up approximately 0.03% of the data on the internet.
Deep Web: The data related to your personal information is stored on the Deep Web. "Google" won't be able to find it, but it's still out there on the World Wide Web. The Dark Web ccontains sites such as your password-protected email account, certain parts of paid subscription services like Hulu, and sites that can be accessed only through an online form. Even though your email account data is on the deep web, it isn't easily accessible to all. According to Brittanica.com, the Deep Web is 400-550 times larger than the public web.
Dark Web: The data stored here is usually encrypted and allows for users and their locations to remain anonymous. The IP addresses of these sites usually requires special software in order to access them. For these reasons, many criminal acts transpire on the dark web as well as political whistle-blower activity which may be censored. According to Brittanica.com, the information found here is approximately 0.01% of the data on the internet.
Investigate these resources to learn more.
![]()
Now that you have an understanding of the different web levels, move on to the next section - Password Managers.

Santeri Viinamäki / CC BY-SA
How strong are your passwords? Check one now using passwordmeter.com.
Most people use very weak passwords and reuse them on different websites. Password leaks occur each year, even on large websites. Malicious individuals could have access to your email, username, address, and password and could access any account where that username or password has been used. In order to help lessen this risk, password managers were developed.
Password managers store your login information for all websites you use and help you log into them automatically. They will also generate strong and unique passwords for all of the websites you visit. Password managers encrypt your password data with only one master password for you to remember. Some of them are available across devices.
Investigate these password managers.
- LastPass - Offers free personal accounts that store and generate passwords and store credit card information for easy online shopping.
- MyKi - Stores passwords on your phone, not in the cloud.
- KeePass - Is a free and open source password manager primarily for Windows.
Finally, investigate this site to see if you could use it with your students. Secure Password Tips from ConnectSafely.org
![]()
Now that you have investigated password managers, move on to the next section - VPN.

https://www.piqsels.com/en/public-domain-photo-jceid
When you use a public network, your security may be at risk. Your activity can be tracked, and hackers can even gain entry into your computer files. A virtual Private Network (VPN) will hide your IP address on a network and will encrypt data to protect it from being intercepted. Read this article by Chris Hoffman to learn more about VPNs, and why you need to have one.
Investigate these VPN services with free versions.
![]()
Now that you have investigated VPNs, move on to the next section - Legalities of Student Data and AUPs.

Atelier-data-privacy CC BY-SA 2.0
It is important that educators understand the laws that govern the collection, sharing, and access to school data. The Family Educational Rights and Privacy Act (FERPA) protects the privacy of student education records. Health Insurance Portability Accountability Act (HIPAA) protects individuals health information, and patient rights regarding health and safety. For more information about FERPA, watch this video. To view/listen, select the image below.
The Children’s Online Privacy Protection Act (COPPA) allows parents to have control over the information that is collected online for their children under the age of 13. It also allows schools to consent on behalf of parents to create accounts and store personal information in online systems, but not for any commercial purposes.
COPPA has several requirements for companies making apps, websites, and online tools for kids under 13. Some key provisions are:
- Provide notice and get parental consent before collecting information from kids
- Have a “clear and comprehensive” privacy policy
- Keep information they collect from kids confidential and secure
You can learn more about Student Privacy laws with FERPA Sherpa and their Educators Guide to Student Privacy.
In order to comply with these regulations, teachers must now also evaluate their online resources for student data use and privacy components. When considering a new online tool, use this checklist template to help you analyze these components. Furthermore, you can check the security of the apps and websites you use in your class by consulting Common Sense Media Security Reviews.
In order to comply with these regulations, most schools require that all stake holders sign an acceptable use policy (AUP). This is a document that outlines the organization's rules for using that organization’s network or the internet and is usually signed by the student or employee before they are granted access to the network or granted a network ID. The AUP is an agreement with the students to keep them safe online and limits their use of the digital world as part of their education, with restrictions to inappropriate or harmful sites or use of school technology for bullying.
Investigate these resources to learn more:
This is the last section of "Thing" 11's Define playlist. Now would be a great time to revisit your Reflection Document and think about what you learned in this "Thing." Capture a screenshot of your results from the Knowledge Check and post them in your Reflection Document. As you move forward, consider the following: How might you use this in your own professional practice? What goals might you set for yourself, including activities, timelines, and evaluation? What connections did you make to the ISTE Standards or your own content area standards? How will you monitor your own progress towards these goals? Then proceed to the next section.